February 2, 2022
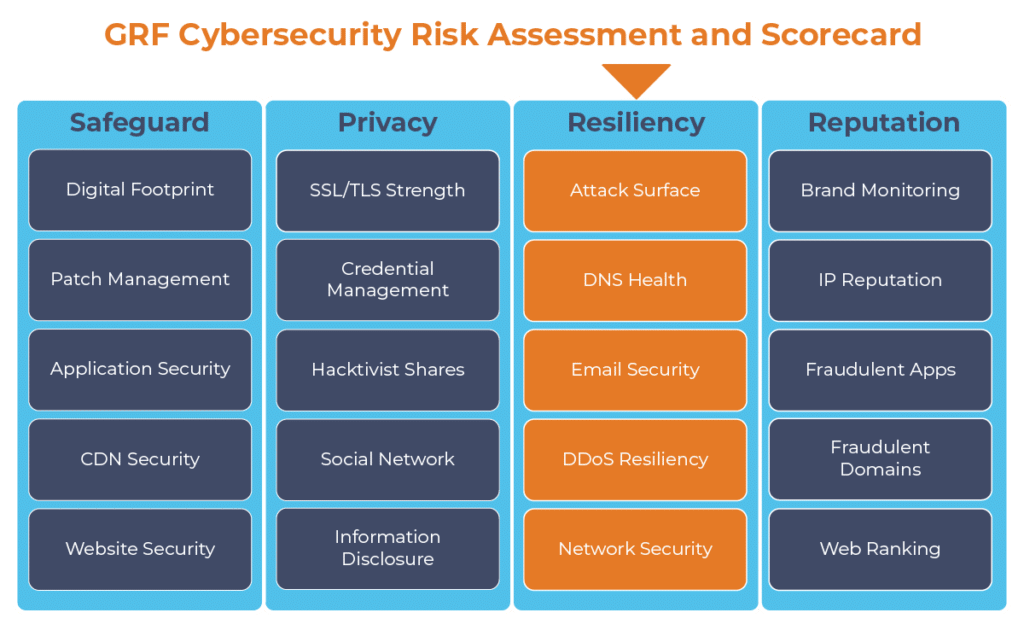
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Your website is essential for promoting your nonprofit organization’s mission. However, bad actors often target nonprofit websites for attack, assuming they are not as protected as commercial sites. One hacker strategy is to bring the site down entirely through a denial of service attack. That’s where checking your DDos resiliency comes in.
A distributed denial of service (DDoS) attack is when a malicious actor (or number of actors) overload your servers to gain access to your website and target your system. This type of brute force attack typically results in blocking access to your applications. Server overloads are not always caused by deliberate attacks. For example, you may experience a website not working when trying to buy a limited-time sale item but the website does not load. This is due to lack of resources on the web server, but the result is the same as a DDoS attack.
Common DDoS Attacks
Volume attacks – These are attacks that send a massive amount of traffic to a site to create either a super slow connection or no connection for legitimate users. This can be done by a coordinated network of attackers visiting your site all at the same time. At GRF, we can help monitor underground forums to learn if your site is are about to be targeted as part of our Cybersecurity Risk Assessment and Scorecard.
Protocol attacks – These attacks overload your server by making numerous server requests. For example, networks often “ping” each other to test connectivity. Hackers can create a “ping flood” to continuously send requests to your server and flood your server with requests, thus causing a volume overload. Another example is a DNS flood, where an attacker sets up pings that target a DNS server (the servers that connect website domain names, or URLs) to the underlying IP addresses. DNS floods disrupt the DNS system, so the website is not reachable.
Application attacks – Attackers can attempt to infiltrate a vulnerability in your application with various attacks. One example is a brute force amplification attack, in which an attacker utilizes a vulnerability in login pages to execute the attack. They will enter in a huge volume of user names and passwords trying to enter your site.
Preventing DDoS Attacks
Common preventative measures you can do to mitigate the risk of DDoS attacks include:
- Patch your system to avoid any potential vulnerabilities.
- Put your web application behind a firewall.
- Utilize Word Press DDoS applications.
- Limit the number of authentication attempts allowed at sign in pages.
- Analyze traffic to identify if a surge is a real spike or an attack.
GRF Can Help
As part of our cybersecurity audits, we offer the GRF Cybersecurity Risk Assessment and Scorecard, which checks your application against 15 common DDoS attack vectors to identify if your organization has any vulnerabilities that may be exploitable. We will look at DNS amplification, Email Server Redundancy, publicly accessible points, and other common vulnerabilities and endpoints.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
For further reading on DDos Attacks: https://cybersecurity.att.com/blogs/security-essentials/types-of-ddos-attacks-explained
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.