July 8, 2021
Experts warn Managed Service Providers (MSPs) and Outsourced IT Providers across the globe to take immediate action
July 9, 2021
While most Americans were celebrating the July 4th holiday, cyber criminals were at it again. In the largest ransomware attack to-date, REvil (aka Sodinokibi) targeted Kaseya and their Virtual System/Server Administrator (VSA) product. Used by Managed Service Providers (MSPs) and Outsourced IT Providers across the globe, Kaseya’s VSA product allows IT departments or MSPs to access computers remotely, push out updates and monitor systems around the world.
The timing of the attack over a holiday weekend allowed the ransomware to propagate undetected within the IT infrastructures of numerous organizations. Some organizations did not notice any issue until encrypted files were discovered when employees returned to work this week.
Background on the Attack
REvil is the same group that made headlines in June for a ransomware attack on meat supplier JBS Foods. This time researchers discovered REvil compromised more than 1,500 Kaseya VSA servers on July 2. With the Kaseya VSA product used for remote management by MSPs around the world, many businesses, large and small, as well as nonprofits and local and state governments are all potentially affected.
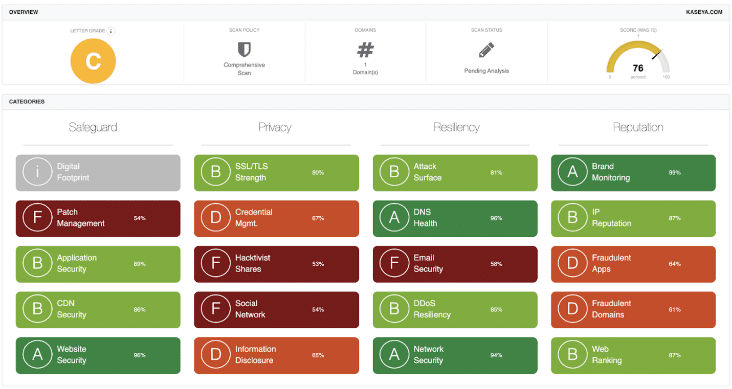
How did this happen? Although the initial entry point is not yet known, the GRF CPAs & Advisors (GRF) Cyber Risk Assessment and Scorecard noted that Kaseya’s cyber rating dropped from a ‘B’ to ‘C’ on an A-to-F rating scale (84 to 76 on a 0-100 numerical scale). The decline was mostly due to poor grades for Patch Management, Credential Management, Application Security, and SSL/TLS Strength. These ratings indicate that threat actors may have potentially accessed some of Kaseya’s systems through:
- Exploiting unpatched vulnerabilities on out-of-date systems;
- Credential-stuffing attacks by using leaked credentials;
- Phishing attacks by exploiting the poor email configuration; and/or
- SQL injection types of attacks on web applications.
Who is at Risk Following the Attack?
In this latest supply chain attack, REvil’s assault on Kaseya’s VSA software provided broad access to the data of organizations throughout the world. One compromised product used by numerous MSPs created a cascading effect, leaving many organizations infected and their data held for ransom. Kaseya has hired FireEye to do a forensic investigation that will provide more information about the impact of the incident. While it will take several weeks or months to understand the full impact, frequent updates on the attack are posted to Kaseya’s website.
Next Steps
If your organization uses the services of an outsourced IT provider or MSP, contact the company immediately to find out if they utilize the Kaseya VSA product. Organizations are also advised to promptly run an internal network scan and conduct a third-party risk assessment for any Kaseya exposure. Delaying these measures could leave your organization open to a possible cyberattack with dire consequences.
Resources
GRF offers clients a variety of cybersecurity tools and resources to protect their organization.
Cyber Risk Assessment and Scorecard
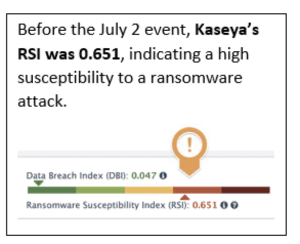
Research indicates that organizations over.50 RSI have a high probability of becoming a victim of cybercrime. With the release of the new Ransomware Susceptibility Index included in GRF’s Cyber Risk Assessment and Scorecard, your organization can assess the likelihood of a ransomware attack on a scale of zero (less likely) to one (highly likely). Watch a demo of the scorecard.
Third-Party Risk Assessment
With many employees continuing to work remotely, we increasingly depend on third-party technologies, external data sources and outside service providers. This makes identifying and managing your organization’s cybersecurity and privacy risks more critical than ever before. For more information about Third-Party Risk Management (TPRM), watch GRF’s webinar, Enhancing Third-Party Risk Management in Cybersecurity & Privacy Programs, and utilize our TPRM checklist.
Publications
GRF’s Cybersecurity Risk Assessment and Scorecard Provides a Holistic Approach to Cybersecurity
Elements of Successful Cybersecurity
An Incident Response Plan Prepares You for a Ransomware Attack
Third-Party Risk in a Post Pandemic World
IT Security is More Critical than Ever for Nonprofits and Associations
Consider a Virtual CISO to Meet Your Current Cybersecurity Challenges
Contacts
If you have questions regarding your organization’s exposure to the Kaseya event or concerns regarding cybersecurity or third-party risk, contact our team below. For more information about managing risk to your organization, visit GRF’s Risk & Advisory Services page.

Partner and Director, Risk & Advisory Services

Senior IT & Risk Analyst