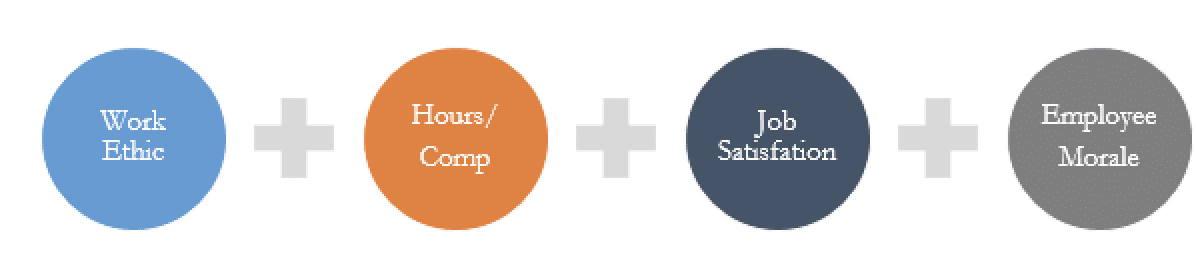October 5, 2021
Keeping it simple provides more protection than you might expect
By Mac Lillard, CPA, CFE, CISA, CRISC, CITP | Manager, Audit and Risk Advisory Services
During 2020, the Federal Trade Commission (FTC) received more than 2.2 million reports of fraud, up 500,000 from the 1.7 million reports filed in 2019. The significant increase in fraudulent activity was largely the result of the shift to virtual work across all industries in response to the COVID-19 global shutdown. The level of business activity now conducted digitally provides additional opportunities for fraud perpetrators to take advantage of organizations.
The pandemic combined with growing social unrest also changed the focus of many organizations. Many shifted their attention from long-term strategic objectives to short-term remedies to cope with economic uncertainty and keep the wheels moving. Accordingly, many organizations either; a) did not have the resources to allocate toward fraud prevention and cybersecurity, or b) failed to recognize the need to allocate resources toward fraud prevention and cybersecurity while addressing the other challenges they were facing.
The Basics of Fraud Control and Prevention
A common misconception about fraud control and prevention is that it is expensive and time-consuming to develop and implement. This could not be more wrong. Some of the strongest fraud controls are inherent in the policies, procedures, and internal controls developed by most organizations. Whether or not these are properly designed and functioning effectively is a different story.
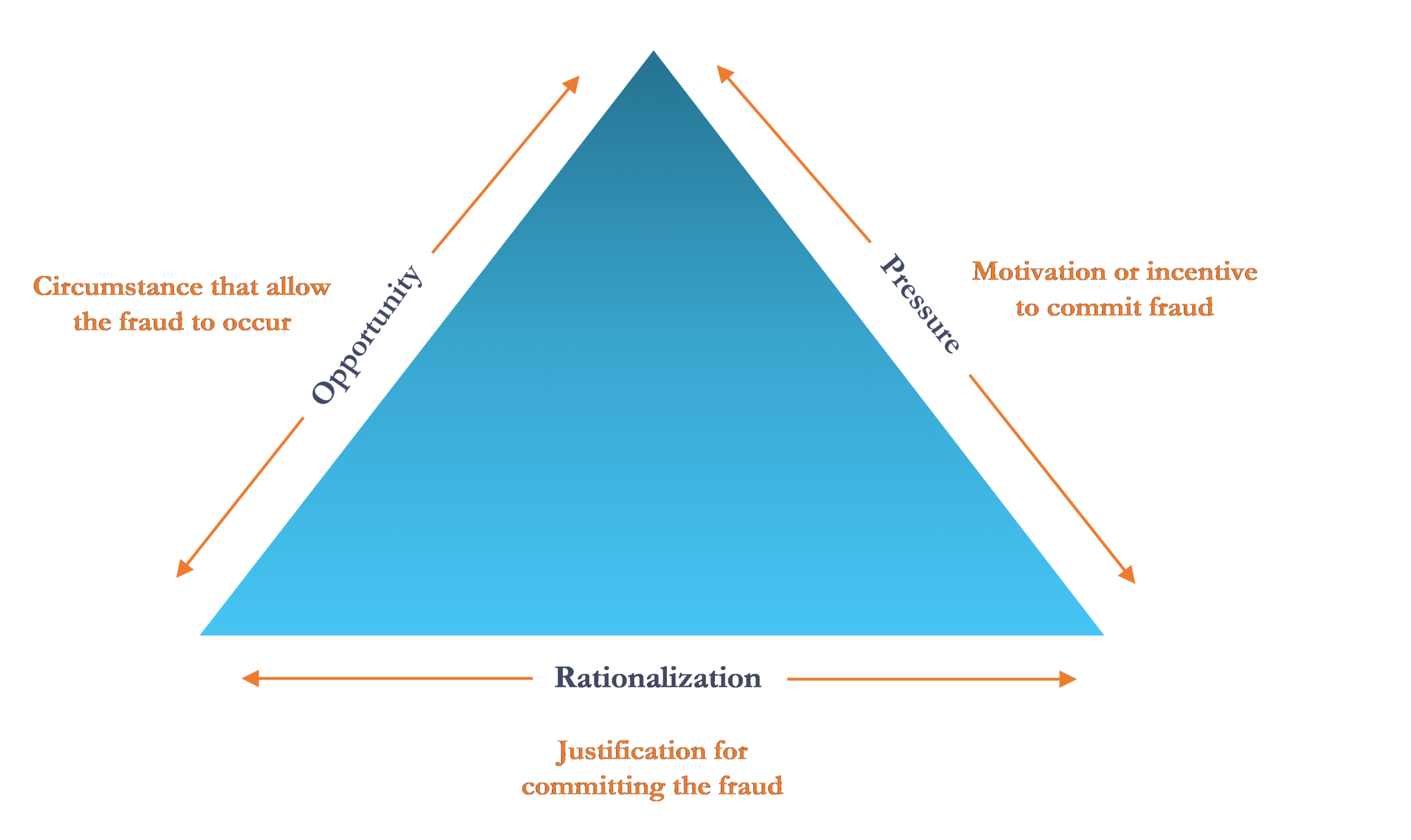
The Fraud Triangle notes the following three elements that give way to fraudulent activity. Anyone or a combination of the three elements can ultimately result in fraudulent activity.
Fraud Triangle
Fraud Prevention Techniques
Basic fraud prevention techniques include low-cost, high-value tools that help minimize the risks associated with the elements of the Fraud Triangle. The most important aspect of each is ensuring that it is custom-tailored to fit your organization’s context and overall risk appetite. Following implementation, these tools must be regularly monitored or evaluated for ongoing effectiveness. Fraud control and prevention is an ongoing process that changes with the organization and the external environment.
Internal Controls
While internal controls might seem like a no-brainer, many times they take a back seat to more critical initiatives during times of rapid change and/or adversity. Strong internal controls reduce the opportunity to commit fraud and serve as a deterrent. Employees aware of strong internal controls will be less motivated to commit fraud for fear of being discovered.
- Review and approval – The segregation of duties on who prepares, approves, and initiates transactions reduces the opportunity for an individual or group of individuals to commit fraud.
- Access Controls – Restricting access to critical systems, sensitive and/or personally identifiable information (PII), and physical locations is essential to minimizing the opportunity for fraudsters to take advantage.
- Mandatory vacation – Requiring employees to take time off reduces the opportunity for fraudsters to conceal their activity when someone must step in to review or assume responsibility for the work.
- Automated Clearing House (ACH) Block –Blocking or restricting transactions that do not meet certain parameters prevents unauthorized ACH payments
- Positive Pay – Authorization for checks not noted on the check file are required to avoid unauthorized check payments
Employee Training
Periodic trainings on code of conduct, employee responsibilities, and the whistleblower process deters fraud and educates employees on how to report suspicious activity. Periodic cybersecurity training is particularly important to train employees how to identify phishing scams and remain current on industry best practices.
Internal and External Cybersecurity Scans
Conducting regular cybersecurity scans is critical to staying ahead of hackers and proactively enhancing your cybersecurity posture. Internal IT departments can acquire these technologies affordably to run on their own systems and organizations who outsource their IT can request their Managed Service Provider or outside consultant provide these services.
Internal Audit
Performing regular assessments of key processes, risk management, and high-risk areas allows the organization to continuously improve and enhance controls to minimize risk on an ongoing basis. Performing these assessments internally is extremely valuable, however, outsourcing or co-sourcing with an independent firm allows the organization to leverage subject-matter experts while allocating their time to their mission and strategic objectives.
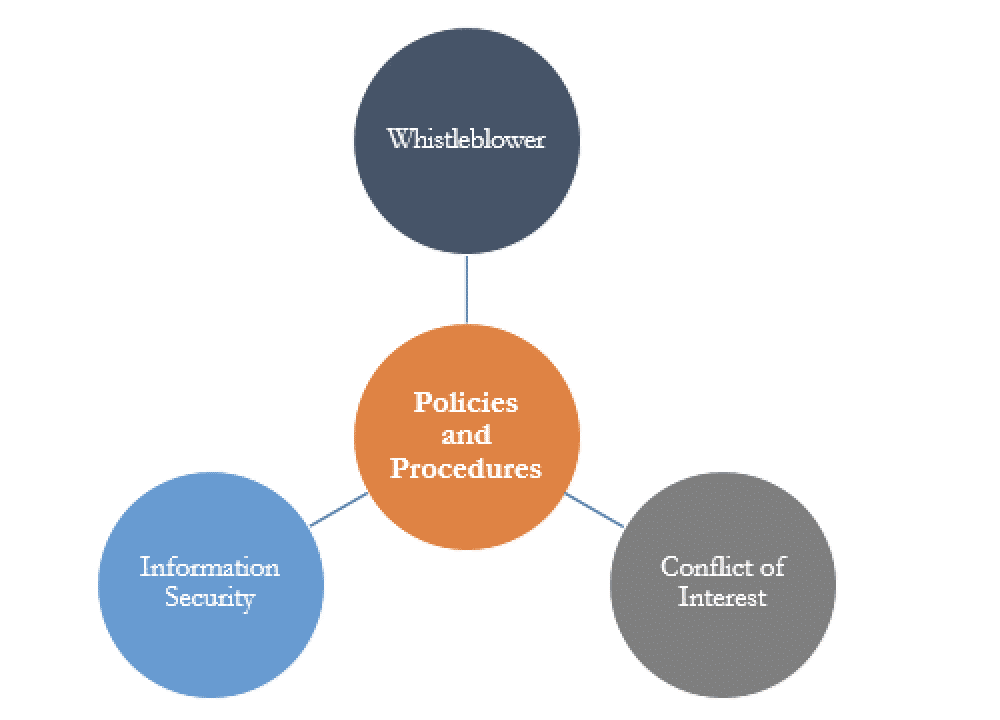
Policies and Procedures
Clearly defined policies and procedures are critical to preventing and deterring fraud. They incorporate internal controls and outline employee responsibilities for ethical and transparent behavior. These policies are particularly important for reducing fraud risk:
- Whistleblower – Outlines the process for individuals to anonymously submit complaints of known or suspicious fraudulent and/or unethical behavior without fear of repercussions.
- Conflict of Interest* – Requires annual attestation from employees and Board members to certify they have no existing relationships that have the potential to affect business decisions.
- Information Security – Outlines the methodology for classifying data and addresses the confidentiality, availability, and integrity of data processed and/or stored by the organization to ensure it is properly protected
*Note: Conflicts of interest do not necessarily preclude business or indicate fraudulent activity. They may be allowed, but only if appropriate measures are taken to mitigate the risk of a preexisting relationship affecting decision-makers. One such method is to require any conflicted individual to recuse themselves from certain business decisions.
Employee Evaluations
Performing regular assessments of employee performance, job satisfaction, and overall well-being provide useful insight to identifying potential fraud perpetrators. The following items should be evaluated through the lens of the Fraud Triangle:
- Work ethic – Employees with little work ethic are more likely to be motivated to commit fraud as an easy meal ticket.
- Hours/Comp – Lack of PTO taken is a red flag for fraudulent activity. Organizations with large wage-gaps are at higher risk of fraud:
- Highly compensated employees have all decision-making power and opportunity to commit fraud
- Lower-level employees are able to rationalize fraud
- Job Satisfaction – Employees who are not satisfied with their job may be more motivated to commit fraud and/or are able to rationalize committing fraud due to their unhappiness.
- Employee Morale – Individually or in the aggregate, low employee morale can lead to motivation/ rationalization to commit fraud. Organizations with widespread low employee morale are at higher risk to fall victim to fraud by collusion.
Proactive Organizations are Better Prepared to Manage Fraud Risk
The operating environment continues to change, new technology is emerging, and fraud schemes are increasing in volume and sophistication. Now more than ever, it is important for organizations to be proactive, not reactive.
Mastering the basics will provide adequate security for most organizations concerned about fraud. Based on the level of perceived risk to the organization, however additional resources may be necessary to effectively mitigate the risk of fraud. Completing a Baseline Fraud Risk Assessment is a great first step for any organization to evaluate their current state, identify high-risk areas and potential vulnerabilities, and shore up policies and procedures.
For more information, visit GRF’s Risk & Advisory Service page and read the second article in the Fraud Control and Prevention series.
Contact

Manager, Risk & Advisory Services
mlillard@grfcpa.com
LinkedIn│Calendly