February 2, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Your email is a critical business function that needs to be constantly available and secured. Securing your email systems involves looking at the configuration of your email server, your mail exchange (MX) records, and SMTP (Simple Mail Transfer Protocol) to identify any potential vulnerabilities or misconfigurations. Identifying these issues before it is too late could help save your organization from being in the news for the wrong reasons.
When it comes to email security, technologies are only part of the equation. The biggest vulnerability is human error. According to security firm KnowBe4, 91% of successful data breaches begin with a simple email that causes the recipient to inadvertently provide an attacker with unauthorized access.
Phishing
Phishing is one of the most common – and successful – forms of email attack. A hacker will fool recipients with fraudulent emails designed to gain personal information such as email passwords, bank accounts, and more. These attacks have increased during the pandemic, so it is important to know what these attacks are, what they look like, and how to prevent them.
Types of Phishing
HTTPS Phishing– These attacks include a legitimate-looking email with a link that directs users to a fraudulent webpage. With the increase in complexity of these attacks, it is harder to distinguish that the link it is a malicious site, as many attackers set up what looks like a secure website that uses HTTPS.
Spear Phishing– An actor targets a specific person and modifies their attack to be personable and appear legitimate. Making the message look like it is coming from a trusted person makes it harder for the recipient to notice that the email, links, or attachments are fraudulent.
Whaling– A form of spear phishing where an attacker goes after a high-profile target such as the CEO of a company.
Vishing– Also known as voice phishing, this is the act of making phone calls that appear legitimate trying to get you to divulge sensitive or personal information like passwords, credit card information, and social security numbers.
Smishing– A newer form of phishing where a text message is used to entice you to click on a link. In a “Bring Your Own Device” (BYOD) environment where employees use one cell phone for personal and business communication, this is particularly dangerous for employers.
System best practices
All organizations should follow email security best practices to avoid the opportunity for human error in their organizational network. There are many configurations that must be set up and analyzed to reduce the risk of attacks through email. It is in the best interest of the organization to create a system that enforces security but also allows for availability and usability.
- Ensure that your SMTP configuration is set up appropriately by testing SMTP Open Relay, Authentication and connection.
- Perform email address spoofing tests.
- If using web mail, make sure you are using a secure connection like SSL.
- Make sure that you have a DMARC (email authentication), DKIM (to prevent spoofing), and SPF record (to limit IP addresses that can use your email domain).
- Have at least two MX servers (email exchange servers) to create redundancy in case one server goes down. This ensures availability of your email.
- Regularly perform tests against your email security to ensure that there are no vulnerabilities.
End user best practices
- Always think before you click on a link on an email. Ask yourself: “was I expecting something from this person?”
- Always check the email sender. The name may appear to be someone you know but look at the actual email address. A sender name can be spoofed, making it dangerous.
- Report malicious emails to your IT team to allow them to pull it from other user’s inboxes or to inform the organization.
- If you do click on a link or download something that seems to be malicious, contact your IT team immediately, as they will need to track your activity and isolate your machine from your network.
- Do not send confidential or sensitive information through email. Always make sure that the information is encrypted and sent through a secure portal.
How GRF Can Help
With more employees working remotely, it is important to make sure that your organization’s communications are safe and secure. As part of our cybersecurity audits, GRF offers a cybersecurity risk assessment and scorecard, which can help ensure your email security is up to date. We will provide you with a scan of your email security, along with 19 other security categories, to identify any potential vulnerabilities or misconfigurations.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
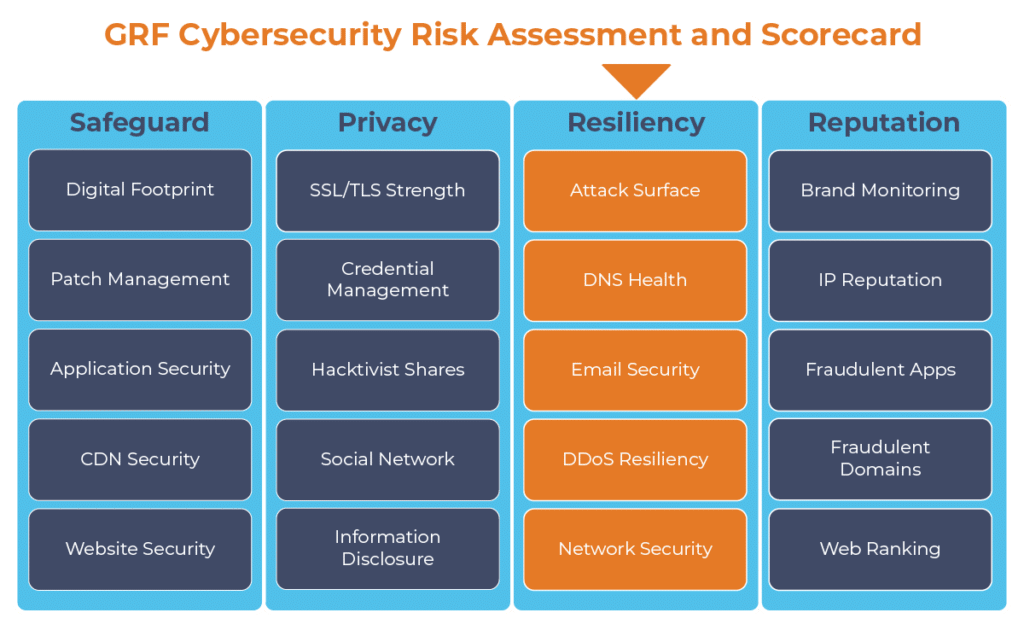
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.