May 17, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
When downloading a new app, be sure it’s from a credible source. Hackers can create fraudulent applications that look very similar in name or appearance to well-known apps. To make matters worse, these fake apps can sometimes be found on trusted sites like the Apple or Google Store as well as being available as a download from the internet. Once these applications are loaded onto a user’s computer, they can perform many attacks to gain data and information and potentially spread their impact across your network.
Attacks from Fraudulent Applications
Fake applications can have a devastating impact on the end-user by launching several kinds of attacks:
- Trojan Horse – This virus performs a script that can infect the computer or network with malware. Because it looks authentic, the user won’t realize it is a virus, which makes this very dangerous.
- Keylogger – This application enables an attacker to track everything a user types, including usernames, passwords, and other sensitive information. They can use the information to harvest the user’s credentials which can lead to unauthorized access to the systems.
- Viruses – These malicious codes can be executed to perform a range of harmful programs that can damage the computer.
How to Mitigate and Reduce Risk
Fake apps that use your logo, name, and brand can fool people into thinking the app is legitimate, resulting in not just a breach of security for the end-user, but a reputation risk for your organization. Follow these best practices to reduce the risk of fraudulent applications affecting you.
- Continuously scan and monitor app stores and the internet to see if there is a new application that is using your organization’s name or logo.
- If pirated apps are found, contact the app store or hosting providers to let them know that the app is fraudulent and should be taken down.
- Monitor your online brand and cyber posture to make sure there aren’t domain names, social media accounts, and other online entities that are very similar to yours. These can be used to target victims.
- Educate your employees so they remain vigilant to potential fraudulent apps.
How GRF Can Help
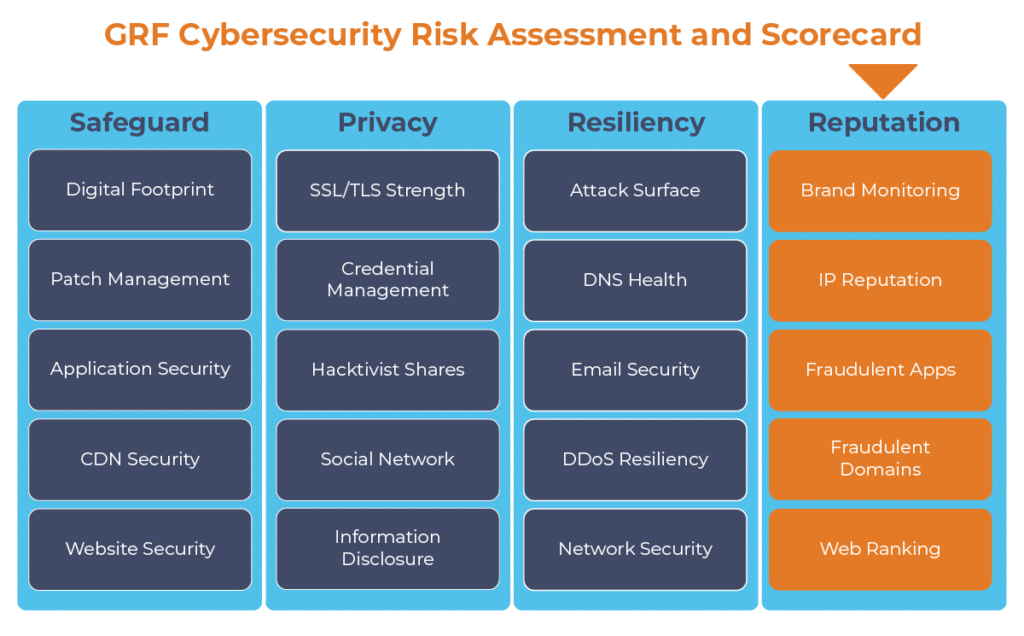
Knowing what fraudulent applications are out there enables you to reduce the opportunity for your users, donors, or website visitors to fall victim to malware from the application. Ongoing Fraudulent Application scanning is one component of our Cybersecurity Risk Assessment and Scorecard, which provides an ongoing scan of your online brand along with 19 other categories to provide best practices and recommendations for improvement.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, CEH, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.