May 17, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Fraudulent domains look very similar to your organization’s domain name and are used to fool people into thinking they are interacting with you. These domains are often used in phishing attacks, which according to CSO Online, account for more than 80% of all reported security incidents. Many phishing attempts come from emails that look legitimate in an attempt to defraud recipients – a tactic commonly referred to as typosquatting. For example, a company name “Example” has an email address of name@example.com. The attacker buys a domain name that closely resembles example.com, such as exammple.com, and sends a malicious email to your employees trying to get them to disclose credential information or pay fake invoices. This is an easy way for malicious attackers to target your organization and potentially cause monetary and reputational harm.
How can you identify these domains?
Two common identifiers of a fraudulent domain are the Levenshtein Distance, a calculation that assesses how close the name is to yours, and Fraudulence Possibility, an indicator that looks at the digital footprint when the domain was created and other domain information which may indicate a malicious intent. Domains that have a fraudulence possibility of over 75% are typically ones that you want to monitor. To find these domains, we can use a tool from ICANN (The Internet Corporation for Assigned Named and Numbers) called WHOIS. This database holds all domains used on the internet. It can be used to test and compare domain names close to yours. While this is a tedious process if done manually, GRF can help by running an external scan and providing a list of the most-likely fraudulent domains.
Best Practices to Avoid Fraudulent Domains
One way to prevent being a victim of a fraudulent domain scam is to register all common typos of your domain name yourself. However, not every organization has the means to buy every possible domain name that is like theirs. At GRF, we recommend the following steps to mitigate the risk:
- Scan your domain against the 300 million + domains in circulation.
- Get a fraudulence possibility score to identify which are the most likely to be dangerous.
- Review the highest risk domains to see what their website is showing.
- Ask these questions of the domains:
- Is the webpage similar or nearly identical to ours?
- Is it a parked website ? These are typically sites with the main page saying, “Coming Soon” or “Under Construction”.
- Could someone mistake this domain name for our organization’s?
- Once you identify the sites that are not legitimate and are risky, you can take action. This list helps identify the most common actions against fraudulent domains:
- Report the domain to the domain registrar noting that it is replicating your website and is not legitimate.
- Buy the domain name if possible.
- On your email server, block emails from being sent to your users from the risky domains.
- Track the domains going forward and do at least a quarterly audit to make sure these domains are not replicating your site.
How GRF Can Help
Knowing what similar domains may be out there will allow you to reduce the opportunity for your users, donors, or website visitors to fall victim to a falsified email or domain. Ongoing Fraudulent Domain scanning is one component of GRF’s Cybersecurity Risk Assessment and Scorecard, a dashboard that continuously monitors internet-facing systems to identify any vulnerabilities.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, CEH, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
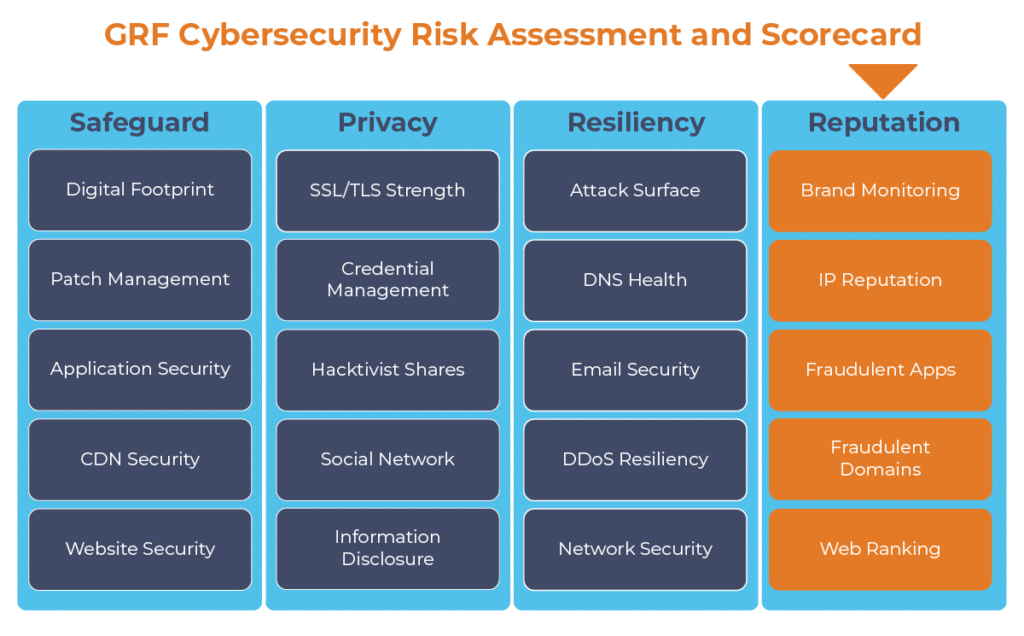
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.