July 20, 2020
By Melissa Musser, CPA, CITP, CISA, Principal, Risk & Advisory Services
While the COVID-19 pandemic has resulted in unprecedented job loss and economic uncertainty around the world, third-party risk is becoming another important headline for businesses and nonprofits. The economic crisis resulting from the pandemic has exposed a number of issues for historically stable and profitable businesses, ranging from early retirement of key executives to insufficient insurance coverage.
Whether a third-party is part of the supply chain or an outsourced information technology services provider, organizations are increasingly implementing third-party risk management (TPRM) programs to ensure third-parties are not creating additional exposure for them. Successful outsourcing relationships with effective risk management allow the organization to safely procure goods and services and focus on their strategic objectives.
What is TPRM?
TPRM is the process of analyzing and mitigating risks associated with parties outside your organization. These parties can include everyone from contractors providing janitorial services to suppliers of a critical component to your manufacturing process. Risks to third-parties are also risks to your organization. A plan for managing third-party risk protects your organization from unsuspected threats and nasty surprises.
Advantages of TPRM Implementation
Implementing a TPRM program takes time and resources, but the advantages far outweigh any cost to the organization.
- Data Breaches – Data breaches are on the rise in 2020 with the distraction of COVID-19 and its aftermath. Even before the pandemic, the first six months of 2019 included over 4 billion records according to Norton in 2019 data breaches: 4 billion records breached so far. Data breaches can include the use of phishing schemes, denial of service, ransomware or malware, and can cost the organization millions of dollars. Even with cyber insurance coverage, each breach costs organizations thousands of dollars to resolve.
- Operational Failures – What if your beloved outsourced accounting firm (who supported your organization for 20 years) suddenly went out of business? Whether the result of unexpected health problems or even death, who will succeed your longtime accountant who knows everything about your finances? You want to understand your service providers’ succession plan before it is too late.
- Vendor Bankruptcy – Your organization depends on a key component in your manufacturing process but that supplier is not answering the phone or replying to emails. With a TPRM program, your organization would know that the company had fallen on hard times and you would have time to identify and procure another supplier for the necessary component. Your manufacturing process stays on-time and within budget.
- Reputational Damage – You read in the news (with everyone else) that your information technology services provider unwittingly helped a foreign country obtain voter registration information. Your organization is connected to this vendor through a legal contract and the relationship made the national headlines. An effective TPRM program would have helped you discovered that the vendor was not maintaining appropriate security measures.
Risk Stratification Guidelines
One of the first steps in any TPRM program is to identify the organization’s most critical vendors and perform the necessary due diligence to assess potential risk in that relationship. As part of the onboarding process for a new vendor or supplier, TPRM stipulates that organizations stratify third-parties into risk tiers based on the offered product or service, as well as the third-party’s location, countries of operation, and other key factors.
Example of Vendor Stratification
Tier 1 – Critical vendors (10%) – PII + critical systems
Tier 2 – Major vendors (40%) – PII OR critical systems
Tier 3 – Vendors (50%) – commodities/low risk purchases
Risk Assessment
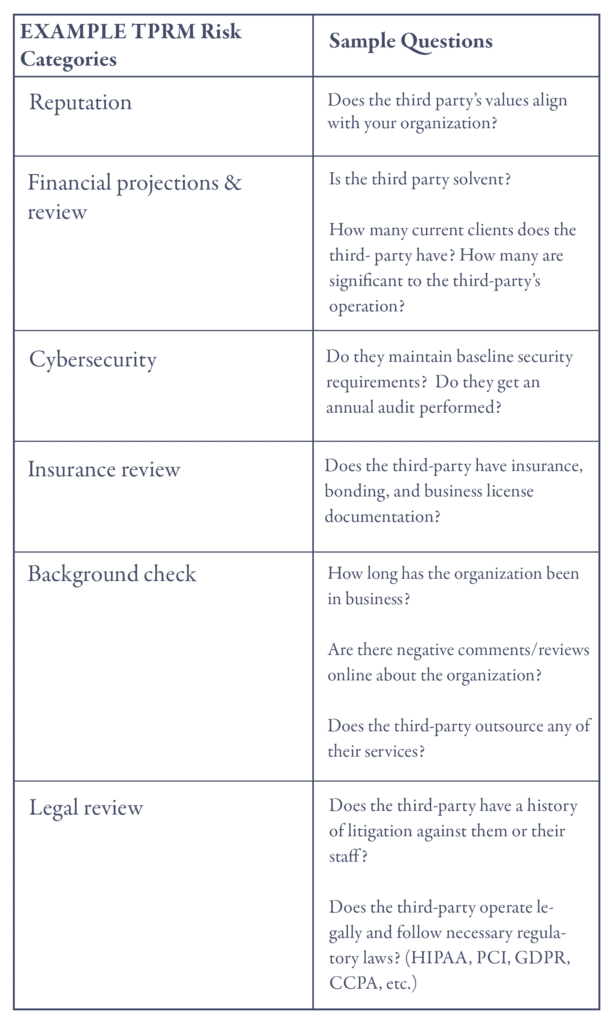
As part of the risk assessment, third-party providers are evaluated in several risk categories. Below are common risk categories and examples of some of the questions used to assess the degree of risk associated with each. Download GRF’s Third-Party Risk Management Checklist for more questions from each risk category to consider during your risk assessment.
Based on the risk assessment, third-parties should be assigned a risk score. This score drives the level of due diligence needed.
Due Diligence for Third-Party Assessment
No one would hire a nanny or baby sitter without first obtaining some essential background information about the individual providing childcare services. The same careful due diligence should be done for any new vendor or supplier of your organization to determine their suitability for the given task.
Due diligence should not just be limited to new third-party providers. It is an ongoing activity, including reviewing, monitoring, and managing communication over the entire vendor lifecycle. As the past few months have taught us, conditions inside and outside of our control can both have a significant effect on operations for any organization. As the buyer of goods and services, you do not want to be surprised when one of your critical vendors cannot deliver on your agreement.
Developing a Third-Party Framework
In general, best practices for any risk management framework include:
- An inventory all third-party vendors your organization has a relationship with (you may need to see who you are paying to find out who they are!);
- An assessment of possible cybersecurity risk exposure from all third-parties;
- Stratifying vendors by tiers by potential risks as described above;
- A system to assess vendors and set a minimum acceptable standards based on the risk assessment guides noted above (as applicable to the specific tiered vendor); and
- Development of contingency plans for when a third-party is deemed below quality or a data breach occurs.
The National Institute of Standards and Technology (NIST) and International Organization for Standardization (ISO) have popular risk management frameworks that can be used together in the assessment process of any third-party risk management program.
Monitoring and Reporting Process for TPRM
Ongoing monitoring and reporting to your organization’s leadership and board of directors will prioritize risk mitigation from your third-parties and facilitate a timely response to risk. To facilitate monitoring and reporting, many organizations employ ongoing analysis and dashboard reporting tools to easily summarize and identify new issues with vendors and suppliers.
Final Takeaway
Competition is healthy and the best practices that should always govern vendor or supplier selection still apply with TPRM. Use GRF’s TPRM Checklist to assist your organization with evaluating a vendor or supplier’s qualifications. The questions will help you identify possible risks upfront to make the best possible purchase decision.
GRF’s Risk & Advisory Services practice offers guidance for a wide range of business and financial issues to support clients through their most challenging business decisions. Contact Melissa Musser, CPA, CITP, CISA, Principal, Risk & Advisory Services at mmusser@grfcpa.com for more information about TPRM and risk to your organization.