October 4, 2021
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Social media has allowed organizations to connect with customers around the world, but the wide reach of your social network also presents opportunities for hackers and bad actors to launch attacks or damage your organization’s reputation. Properly understanding and managing your social media presence allows you to mitigate risks and build a brand image that people in the community know and respect.
Social Network and Cybersecurity risk?
Many social media applications, such as Twitter, Facebook, Reddit, and Discord give people a way to communicate with many people that they never would have been able to connect with in the past. Hackers capitalize on this by trying to gain publicity and rally a group of people to attack a targeted organization. The attacker’s motivation can be anything from disagreeing with your message to just practicing their skills.
The most common cyber-attack that can occur from a social media influence is a denial-of-service attack. A group of attackers attempts to bring down your website by visiting the site or sending a flood of emails all at once, thus negating access to either your corporate network or your website. Being aware of when an attack is coming allows you to prepare by filtering IP addresses to look for legitimate connections.
What are some other social media risks?
While attackers can use social media to gain support for their cause, your users need to be aware of their actions on social media as well. Their actions can have serious risks to both the security and reputation of your organization. For example, security can be compromised when a user gives away too much personal information to someone they do not know, leaving their account potentially vulnerable to being infiltrated. Additionally, a user on social media can post anything that is on their mind, so if they decide to talk poorly about your organization, it can harm how the public view both the organization and the employees. Some other risks include:
- Third-party credential breaches
- Clicking on malicious links to infect computers
- Exposing confidential information
- Phishing
- Brand impersonation
How can you limit these risks and take advantage of social media?
Things that an organization can do to take advantage of social media and reduce their risk include:
- Create a social media policy that identifies what can be posted about the organization.
- Screen employee’s social media presence during the hiring process.
- Scan social networks for your organization’s name to look for the conversation around your organization.
- Respond quickly when customers interact with you.
How GRF can help
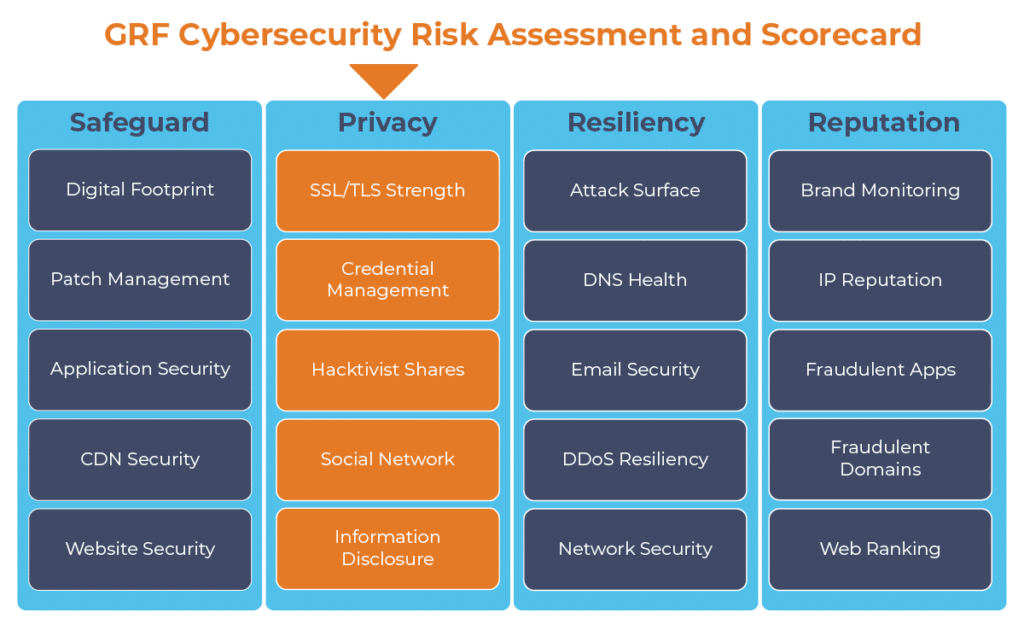
Social networks are not going anywhere any time soon, so it is important to track what is being said about you and monitor activity so you know when an attack may be coming. As part of our cybersecurity audits, we offer our Cybersecurity Risk Assessment and Scorecard, a dashboard that continuously monitors internet-facing systems to identify any vulnerabilities. One component of the scorecard continuously tracks social networking to see what is being said about the organization, looking for words like “hack”, “breach”, or “leak”.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.