February 2, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
It’s not just about disruption or inconvenience. A compromised technology incident can have a detrimental impact on your organization’s processes, mission, and reputation. A review of your external network security risk should include looking at any risk that is related to your perimeter network – or how users gain access to your organization’s data.
Network Security is comprised of the policies and procedures an organization utilizes to prevent and monitor against unauthorized access, misuse, modification, or denial of a computer network. It also provides procedures for maintaining the confidentiality, integrity, and availability of data.
Most Common Network Attacks
Network attacks attempt to gain access to information or assets that should be confidential. Many network-level problems stem from open critical ports, unprotected network devices, misconfigured firewalls, and service endpoints. There are two types of network attacks: passive and active. A passive attack is when a malicious attacker intercepts data traveling through your network to gain information. An active attack occurs when a malicious attacker runs commands to disrupt the normal operation of your network or to gain access to devices on the network. Some of the most common types of attacks include:
Unauthorized Access
When maintaining confidentiality, integrity, and availability of information, it is important to control who should have access to what information. When a malicious attacker gains access to your network, they can steal, modify, or lock down information.
Denial of Service
Malicious attackers can target a network and flood it with service requests. The overload on your servers can cause a denial of service and bring your network or database down. This will not allow legitimate users to access your site which can result in a loss of funding, subscribers, and organizational growth.
Man in the Middle
A man-in-the-middle attack is the interception of traffic between your network and other websites. If the transmitted data is not encrypted, an attacker can gain access to data that is being sent and steal or change the information. For example, an attacker might steal the data being transmitted to gain a user’s credentials.
What is at risk from a network attack?
Customer information: When your network is not secure, you risk exposing personally identifiable information about a customer or donor. Attackers can “sniff” your network for vulnerabilities and steal credential information which can leave your organization vulnerable to unauthorized access to organizational, customer, and financial information.
Revenue: If your site is brought down, legitimate users cannot access your site to make donations, register for events, or join as members. Having mitigation procedures in place to avoid the risk of denial of service attacks is critical to ensuring high availability for your website and network.
Mission: Attacks that ruin your organization’s reputation can have devastating and long-lasting effects – from loss of donors, to employee turnover, to diminished public support. It is essential to make sure that data is kept in a secure, encrypted space to avoid the risk of losing the public’s trust.
Ransomware: If a malicious actor can exfiltrate data due to a vulnerability or a weakness in your network security, your organization risks all of the above. During a ransomware attack, a malicious actor introduces malware to the network to lock critical data and systems, bringing your organization to a screeching halt.
Mitigating Network Risks
To understand what a malicious attacker sees, perform regular external network assessments to identify potential vulnerabilities like open ports or services that are missing data encryption. You should also regularly look at your network setup for handling ping floods (attempts at a DDos attack) and firewalls.
When you identify risks and vulnerabilities, there are many ways you can reduce the likelihood that they impact your organization. Some common remediation actions that are utilized after running an external network scan include:
- Disabling plaintext protocols like telnet or HTTP
- Monitor publicly available ports and close unused critical ports
- Having web applications behind a firewall
- Blocking attacks on your internet network (UDP Flood, ICMP flood, etc.)
- Disabling Anonymous FTP logins
While this is not everything that you must consider, they are a starting point for preventing some of the most common attacks and risks.
How GRF Can Help
As part of our cybersecurity audits, we offer a Cybersecurity Risk Assessment and Scorecard that assesses your network and provides a list of all the possible vulnerabilities. It provides remediation recommendations and ranks the risks from highest to lowest.
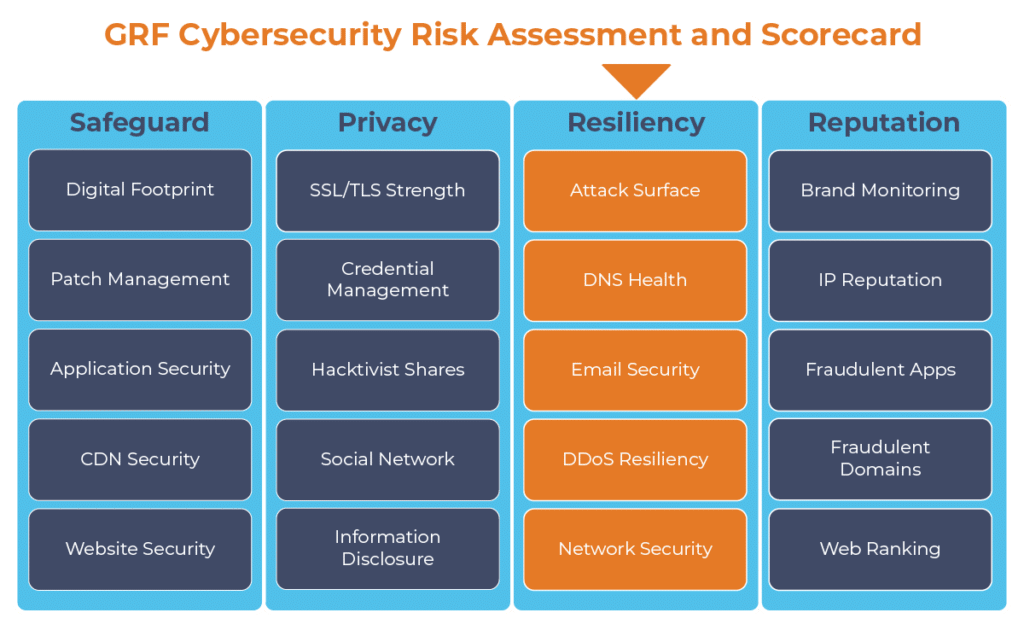
Cybersecurity should take a holistic approach to mitigate risks. While network security is important, there are other areas of potential vulnerabilities that our team can help you to identify and mitigate. The GRF Cybersecurity Risk Assessment and Scorecard identifies possible vulnerabilities and weaknesses of an organization by evaluating 19 security related categories and one informational category. Each of the categories impact the score and help to create an easy to read report. The report will identify possible risks, remediation steps, and best practices to increase your score.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
For further reading on network security:
https://www.geeksforgeeks.org/active-and-passive-attacks-in-information-security/
https://www.cynet.com/network-attacks/network-attacks-and-network-security-threats/
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.