February 2, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Your organization’s domain name (e.g. “example.com”) serves as the base of operations for your online identity – helping interested parties to find you and connect with you online. However, the underlying machine language of the internet is based on numbers. Every site on the internet has a unique location identifier called an IP address. The domain name system (DNS) serves as a translator – mapping the language-based domain names to their corresponding IP addresses and then routing requests accordingly. This makes it easier for people to find websites, companies, and things they are interested in online. Without DNS, we would have to remember hundreds of IP addresses for everything, rather than just remembering domain names.
DNS servers make life easier, but they also provide an opening for unwanted attacks. One of the reasons attackers target your DNS is because it is often not secured and successful attacks can be profitable and cause disruption. If your DNS is poorly configured or insecure, it could be an easy target for an attacker. Regularly reviewing your DNS health allows you to identify any missing configurations and create an appropriate defense against attackers who may try to take down your critical business functions.
How are DNS Servers attacked?
Some of the most common attacks include DDoS attacks, domain name hijacking, and DNS amplification attacks.
A Distributed Denial of Service attack (DDoS) or a simple denial of service (DoS) attack is achieved when bad actors send so many requests to your domain server all at once that it is not able to handle them. This causes your website to become unresponsive to legitimate requests (read more on our blog post on DDoS Attacks).
Domain name hijacking occurs when an attacker gains control of your domain name by transferring it from your registrar (for example GoDaddy) to their registrar account. Once this is done, they can simply redirect your web traffic to a site of their choosing, potentially one that looks exactly like yours but with malicious links and or software. As mentioned previously it is easier for people visiting your website to remember the site name instead of an IP address (104.2.45.186) because of this an attacker can keep your website name the same while changing the IP address on the backend.
DNS amplification attacks are a type of DDoS attack in which a DNS system is exploited and turns smaller requests into larger ones, thus overloading servers.
Understanding these types of attacks and scanning your DNS is beneficial in preventing your organization from falling victim.
What items should be scanned for DNS Health?
Some tests that can be run include NS tests, parent server tests, MX tests, WWW tests and SOA tests. Each of these tests help to identify whether your organization is following best practices when setting up and maintaining your DNS. Some common things to review include your domain’s MX record redundancy, making sure your WHOIS registry and registrar fields correctly configured, and reviewing DNSSEC records.
MX record redundancy– When your primary mail server is down, it is crucial to have a backup record – called a mail exchange record (MX record) – to allow you to continue to accept mail. Since email is one of the main forms of business communication, having this set up with redundancy will reduce down time in the event of mail server disruption.
DNS Registry and registrar records enable multi factor authentication on your domain name for added security. You can set up alerts, so you are notified if your domain name information is deleted, transferred, or updated. This prevents attackers from secretly hijacking your domain and changing your website to a malicious one.
DNSSEC records help to secure DNS records by adding a layer of trust on top of DNS. They provide authentication of DNS data, ensuring the data integrity is maintained and proper authentication is exchanged between DNS servers and clients.
How GRF Can Help
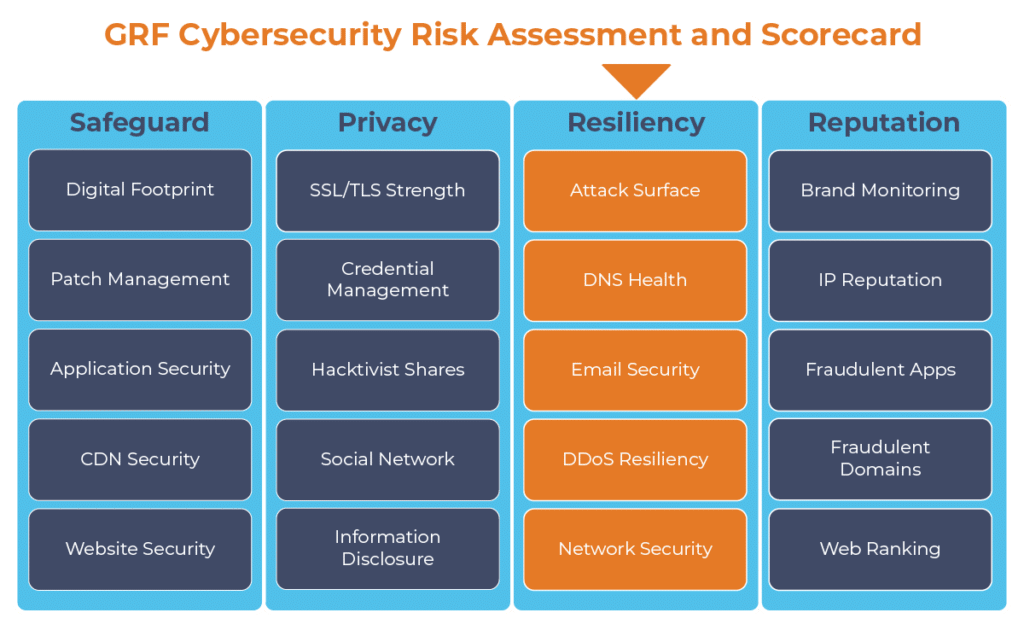
At GRF, we can help identify these misconfigurations in your DNS and create a secure DNS. As part of our cybersecurity audits, our Cybersecurity Risk Assessment and Scorecard scans your DNS and provides mitigation steps for the items that are missing. The scorecard also includes 19 other categories to increase your organization’s cybersecurity.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.