May 17, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Your organization’s reputation can be influenced by a variety of factors including brand image, online reviews, social media presence, customer experience, and more. Each of these elements factors into the overall image of the organization. When it comes to your internet reputation, important elements are different and can impact not just how you are seen by the public, but if you are seen at all. Your organizational domain and IP reputation is rated on factors such as presence on blacklists, use of botnets, and the reputation of the URLs owned. Each of these elements creates an overall reputation for your organization and can influence how your website shows up on search results or how your emails are delivered.
Understanding Your Cyber Reputation
To combat the enormous amount of spam email sent every day, Internet Service Providers create blacklist databases that identify IP addresses that send spam, send malicious files, or have been reported for cyber abuse in the past. These lists are used by many organizations to filter out suspicious emails sent to their end-users. If your organization’s IP address is listed on an IP reputation database like abuseipdb.com, legitimate emails sent by your employees could be blocked by the recipient organization’s email filtering service. Your emails might never make it to the intended recipient.
It is important to monitor these IP reputation databases so you can identify possible email delivery issues and try to remove the listing of your IP address if it appears.
Your IP address could become blacklisted without your knowledge. An end-user on your system could accidentally click on a malicious link that downloads a computer virus, giving control to a hacker. The hacker can then use the computer to send emails in the background or add it to a botnet for denial-of-service attack on another computer system.
Some of the riskiest assets that an organization can hold are IP addresses and domains that are not actively managed. For example, if a systems administrator purchases a domain name and associated IP address but forgets about it or does not manage it, this domain could fall victim to a hacker, resulting in a bad cyber reputation for your organization across the internet.
Remediation Steps to Consider
There are several things that your organization can do to build a healthy, trusted cyber reputation. Continuously tracking and understanding where your organization is seen on the internet is the goal of the remediation steps.
- Regularly monitor IP reputation databases. When your domain’s IP address is listed on a blacklist database do the following:
- Determine if this is a false positive or something malicious.
- Contact the site to request your IP address be removed from the list.
For example, on abuseipdb.com, you can search your IP address, and if it is found, submit a request through their link to have it taken off.
- Set up email filtering and firewalls using the IP address blacklist databases to block spam and malicious traffic coming to your users.
- Make sure that domains that you own resolve back to a trusted IP address.
While you cannot always prevent someone from reporting your organization, you can ensure that your organization is not on these databases by monitoring the lists and having your IP address removed if it appears.
How GRF Can Help
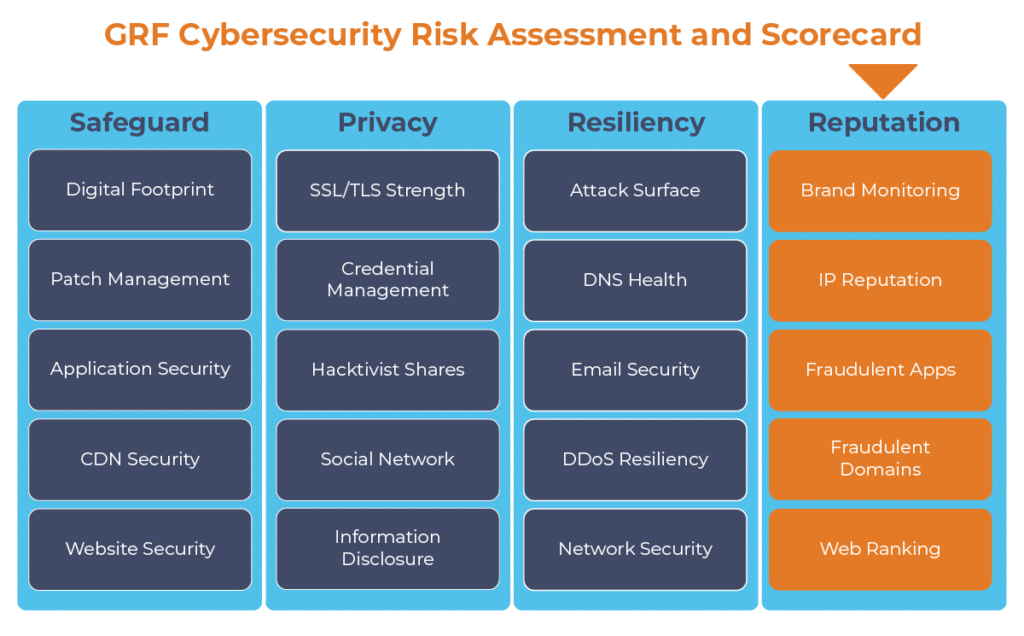
The persistent threat of being listed as spam, included in a botnet, or categorized as dangerous can cause problems for your organization. Through scanning and querying your organization’s name and web domains, GRF can help to provide updates and alerts on your organization’s IP reputation. As one component of our cybersecurity audits, our Cybersecurity Risk Assessment and Scorecard will provide an ongoing scan of your online brand along with 19 other categories to provide best practices and recommendations for improvement.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, CEH, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.