February 2, 2022
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Anything freely available on the internet and open to users can be a point of attack for a malicious actor. To prevent unauthorized access to your network and systems, it’s crucial to understand the vulnerabilities of your network.
The term “attack surface” refers to the total number of access points into your system. An attacker can scan the internet to look for information about your site and if they see something that looks vulnerable, they could come knocking. Securing your systems from unauthorized access starts with analyzing for open critical ports, outdated services, SSL/TLS strength, and other misconfigurations that can come from unpatched servers or from testing and troubleshooting. Securing all access points, knowing what is vulnerable, and developing a proactive security strategy can help your organization prevent cyberattacks.
Critical Points
While it is important to constantly scan for vulnerabilities on your network and servers, there are places within the network that can be particularly risky if vulnerable.
Open Critical Ports – These are access points, or ports, that are open to the public and allow for remote administration. Some examples of this are Microsoft’s Remote Desktop Protocol (RDP), Virtual Network Computing system (VNC), the Secure Shell Protocol (SSH), the Telnet application, and Simple Network Management Protocol (SNMP). With the shift to remote work and remote administration, these ports are now commonly used, so they need to be locked down to only trusted IP addresses and secured through strong cryptography and security protocols.
Outdated Systems – Having outdated service versions or servers can provide an opportunity for attackers to use a known vulnerability against you. This relates directly to your patch management policy along with tracking end-of-life server versions. Patch management can be done monthly and should be tested before implementation. When the vulnerabilities are known, your organization should be consistently updating versions and applying the appropriate patches. Similarly, if a server is going to be at end of life (such as Server 2008 r2), then you should start planning the migration of the data or applications from that server to a new one.
Web applications – Many vulnerabilities can be exploited through a web application. Common exploits include cross-site request forgery, SQL injections, brute force password attacks, and more. Each of these presents the risk of an attacker gaining unauthorized access to your information or systems.
Outdated security protocols – Many web browsers do not allow users to access a site if it is not secure (a secure site has a web address starts with https:// and a lock icon appears in the address window). Even if your site has a valid SSL certificate – indicating that data is properly encrypted on your site – there still may be out-of-date security protocols that make you vulnerable. One of the most common examples is having older Transport Layer Security (TLS) versions enabled. TLS is a protocol designed to encrypt data sent over the internet, but like software, it is regularly updated to address identified vulnerabilities. At this point, TLS 1.2/1.3 are the only TLS versions that should be enabled on your site. Finally, you should verify that the cipher suite you are using is also updated. The cypher suite is the set of algorithms available for networks to secure a connection. Even if you have an updated TLS, using weak ciphers can leave you open to common SSL/TLS attacks.
How GRF Can Help
With so much information exchanged online, it is important to understand what information is readily available to potential hackers. This will help your organization identify vulnerabilities and mitigate its risk of being attacked. Knowing critical points is a good start, but new access points can be created and identified by bad actors all the time. Ongoing scanning is recommended to create a proactive security stance against malicious attackers.
At GRF, as part of our cybersecurity audits, we offer a cyber risk assessment and scorecard that continually scans for vulnerabilities and provides easy-to-implement and follow mitigation steps. With the increase of online activity, making sure that your organization is thinking like a hacker can help to prevent attacks from being successful.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
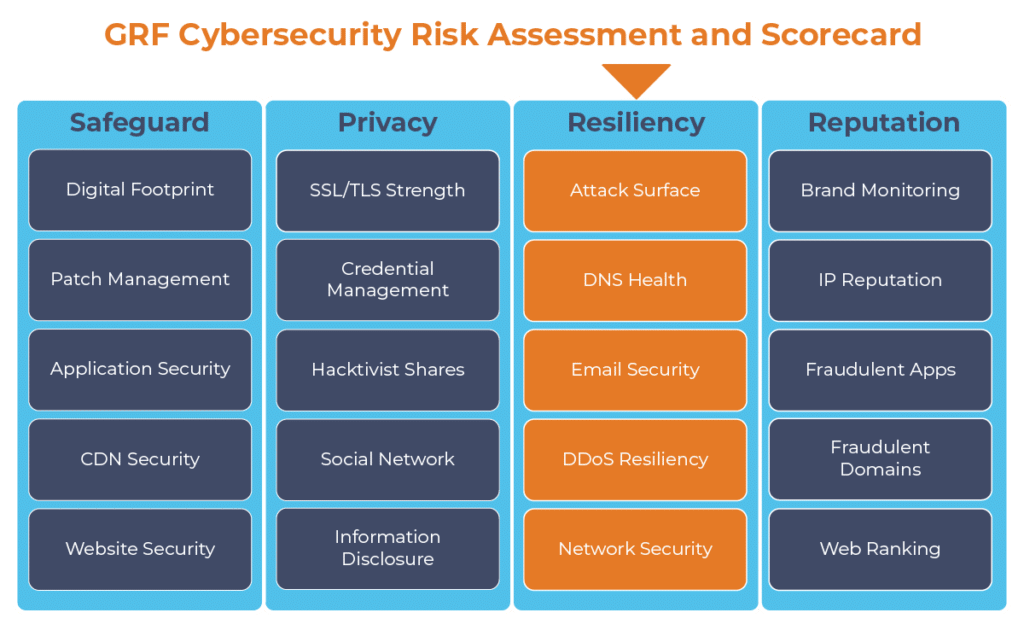
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.